The Next NSA Spying Shoe to Drop: “Pre-Crime” Artificial Intelligence ~ hey besides the spying(control files on whoever) & the deep,deep DEEP finance system ? & c'ing who has,does what wit the 'new' technology (coming down the pike(hint,hint ..new "phisss~icks" maybe just maybe ALL the spy~in IS "they" r look~in fer somebody who kinda looks like US ...& IS kinda "close" 2 US ....but isn't from round here ....but is here & more r coming here (or R on "their" way here ) ..just a thought & ALL this smoke is just cover 4 THAT ? & maybe just maybe Y all the "spraying " ALL over the Planet ....ya know 2 make IT kinda un~bear~able ( or reveals them ?) .... they know some~body IS coming ...back ...soon ? hummmmmmmmmmmm
:o Oops

NSA spying whistleblower Edward Snowden’s statements have been verified. Reporter Glenn Greenwald has promised numerous additional disclosures from Snowden.
What’s next?
We reported in 2008:
A new article by investigative reporter Christopher Ketcham reveals, a governmental unit operating in secret and with no oversight whatsoever is gathering massive amounts of data on every American and running artificial intelligence software to predict each American’s behavior, including “what the target will do, where the target will go, who it will turn to for help”.PBS Nova reported in 2009:
The same governmental unit is responsible for suspending the Constitution and implementing martial law in the event that anything is deemed by the White House in its sole discretion to constitute a threat to the United States. (this is formally known as implementing “Continuity of Government” plans).
As Ketcham’s article makes clear, these same folks and their predecessors have been been busy dreaming up plans to imprison countless “trouble-making” Americans without trial in case of any real or imagined emergency. [Background here.] What kind of Americans? Ketcham describes it this way:
“Dissidents and activists of various stripes, political and tax protestors, lawyers and professors, publishers and journalists, gun owners, illegal aliens, foreign nationals, and a great many other harmless, average people.”Do we want the same small group of folks who have the power to suspend the Constitution, implement martial law, and imprison normal citizens to also be gathering information on all Americans and running AI programs to be able to predict where American citizens will go for help and what they will do in case of an emergency? Don’t we want the government to — um, I don’t know — help us in case of an emergency?
Bear in mind that the Pentagon is also running an AI program to see how people will react to propaganda and to government-inflicted terror. The program is called Sentient World Simulation:
“U.S defense, intel and homeland security officials are constructing a parallel world, on a computer, which the agencies will use to test propaganda messages and military strategies.Called the Sentient World Simulation, the program uses AI routines based upon the psychological theories of Marty Seligman, among others. (Seligman introduced the theory of ‘learned helplessness’ in the 1960s, after shocking beagles until they cowered, urinating, on the bottom of their cages.)The continuity of government folks’ AI program and the Pentagon’s AI program may or may not be linked, but they both indicate massive spying and artificial intelligence in order to manipulate the American public, to concentrate power, to take away the liberties and freedoms of average Americans, and — worst of all — to induce chaos in order to achieve these ends.
Yank a country’s water supply. Stage a military coup. SWS will tell you what happens next.
The sim will feature an AR avatar for each person in the real world, based upon data collected about us from government records and the internet.”
The National Security Agency (NSA) is developing a tool that George Orwell’s Thought Police might have found useful: an artificial intelligence system designed to gain insight into what people are thinking.World Net Daily’s Aaron Klein reported earlier this month:
With the entire Internet and thousands of databases for a brain, the device will be able to respond almost instantaneously to complex questions posed by intelligence analysts. As more and more data is collected—through phone calls, credit card receipts, social networks like Facebook and MySpace, GPS tracks, cell phone geolocation, Internet searches, Amazon book purchases, even E-Z Pass toll records—it may one day be possible to know not just where people are and what they are doing, but what and how they think.
The system is so potentially intrusive that at least one researcher has quit, citing concerns over the dangers in placing such a powerful weapon in the hands of a top-secret agency with little accountability.
Known as Aquaint, which stands for “Advanced QUestion Answering for INTelligence” [which is run by the Intelligence Advanced Research Projects Activity (IARPA)], part of the new M Square Research Park in College Park, Maryland. A mammoth two million-square-foot, 128-acre complex, it is operated in collaboration with the University of Maryland. “Their budget is classified, but I understand it’s very well funded,” said Brian Darmody, the University of Maryland’s assistant vice president of research and economic development, referring to IARPA. “They’ll be in their own building here, and they’re going to grow. Their mission is expanding.”
***
In a 2004 pilot project, a mass of data was gathered from news stories taken from the New York Times, the AP news wire, and the English portion of the Chinese Xinhua news wire covering 1998 to 2000. Then, 13 U.S. military intelligence analysts searched the data and came up with a number of scenarios based on the material. Finally, using those scenarios, an NSA analyst developed 50 topics, and in each of those topics created a series of questions for Aquaint’s computerized brain to answer. “Will the Japanese use force to defend the Senkakus?” was one. “What types of disputes or conflict between the PLA [People's Liberation Army] and Hong Kong residents have been reported?” was another. And “Who were the participants in this spy ring, and how are they related to each other?” was a third. Since then, the NSA has attempted to build both on the complexity of the system—more essay-like answers rather than yes or no—and on attacking greater volumes of data.
“The technology behaves like a robot, understanding and answering complex questions,” said a former Aquaint researcher. “Think of 2001: A Space Odyssey and the most memorable character, HAL 9000, having a conversation with David. We are essentially building this system. We are building HAL.” A naturalized U.S. citizen who received her Ph.D. from Columbia, the researcher worked on the program for several years but eventually left due to moral concerns. “The system can answer the question, ‘What does X think about Y?’” she said. “Working for the government is great, but I don’t like looking into other people’s secrets.
A supersmart search engine, capable of answering complex questions such as “What were the major issues in the last 10 presidential elections?” would be very useful for the public. But that same capability in the hands of an agency like the NSA—absolutely secret, often above the law, resistant to oversight, and with access to petabytes of private information about Americans—could be a privacy and civil liberties nightmare. “We must not forget that the ultimate goal is to transfer research results into operational use,” said Aquaint project leader John Prange, in charge of information exploitation for IARPA.
Once up and running, the database of old newspapers could quickly be expanded to include an inland sea of personal information scooped up by the agency’s warrantless data suction hoses. Unregulated, they could ask it to determine which Americans might likely pose a security risk—or have sympathies toward a particular cause, such as the antiwar movement, as was done during the 1960s and 1970s. The Aquaint robospy might then base its decision on the type of books a person purchased online, or chat room talk, or websites visited—or a similar combination of data. Such a system would have an enormous chilling effect on everyone’s everyday activities—what will the Aquaint computer think if I buy this book, or go to that website, or make this comment? Will I be suspected of being a terrorist or a spy or a subversive?
In February, the Sydney Morning Herald reported the Massachusetts-based multinational corporation, Raytheon – the world’s fifth largest defense contractor – had developed a “Google for Spies” operation.Aaron Klein reported last week that Snowden might have worked at the NSA’s artificial intelligence unit at the University of Maryland:
Herald reporter Ryan Gallagher wrote that Raytheon had “secretly developed software capable of tracking people’s movements and predicting future behavior by mining data from social networking websites” like Facebook, Twitter, and Foursquare.
The software is called RIOT, or Rapid Information Overlay Technology.
Raytheon told the Herald it has not sold RIOT to any clients but admitted that, in 2010, it had shared the program’s software technology with the U.S. government as part of a “joint research and development effort … to help build a national security system capable of analyzing ‘trillions of entities’ from cyberspace.”
In April, RIOT was reportedly showcased at a U.S. government and industry national security conference for secretive, classified innovations, where it was listed under the category “big data – analytics, algorithms.”
Jay Stanley, senior policy analyst for the ACLU Speech, Privacy and Technology Project, argued … that among the many problems with government large-scale analytics of social network information “is the prospect that government agencies will blunderingly use these techniques to tag, target and watchlist people coughed up by programs such as RIOT, or to target them for further invasions of privacy based on incorrect inferences.”
“The chilling effects of such activities,” he concluded, “while perhaps gradual, would be tremendous.”
Ginger McCall, attorney and director of the Electronic Privacy Information Center’s Open Government program, told NBC in February, “This sort of software allows the government to surveil everyone.
“It scoops up a bunch of information about totally innocent people. There seems to be no legitimate reason to get this, other than that they can.”
As for RIOT’s ability to help catch terrorists, McCall called it “a lot of white noise.” [True ... Big data doesn't work to keep us safe.]
The London Guardian further obtained a four-minute video that shows how the RIOT software uses photographs on social networks. The images, sometimes containing latitude and longitude details, are “automatically embedded by smartphones within so-called ‘exif header data.’
RIOT pulls out this information, analyzing not only the photographs posted by individuals, but also the location where these images were taken,” the Guardian reported.
Such sweeping data collection and analysis to predict future activity may further explain some of what the government is doing with the phone records of millions of Verizon customers. [Background here.]
***
“In the increasingly popular language of network theory, individuals are “nodes,” and relationships and interactions form the “links” binding them together; by mapping those connections, network scientists try to expose patterns that might not otherwise be apparent,” reported the Times. [Background here.]
In February 2006, more than a year after Obama was sworn as a U.S. senator, it was revealed the “supposedly defunct” Total Information Awareness data-mining and profiling program had been acquired by the NSA.
The Total Information Awareness program was first announced in 2002 as an early effort to mine large volumes of data for hidden connections.
Edward Snowden, the whistleblower behind the NSA surveillance revelations, told the London Guardian newspaper that he previously worked as a security guard for what the publication carefully described as “one of the agency’s covert facilities at the University of Maryland.”
***
Brian Ullmann, the university’s assistant vice president for marketing and communications, was asked for comment. He would not address the query, posed twice to his department by KleinOnline, about whether the NSA operates covert facilities in conjunction with the university.
Ullmann’s only comment was to affirm that Snowden was employed as a security guard at the university’s Center for the Advanced Study of Languages in 2005.




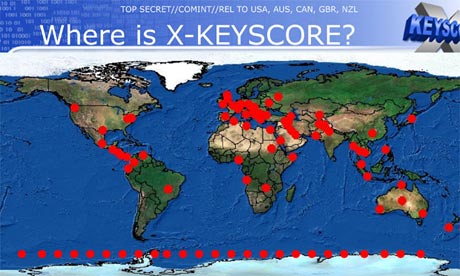
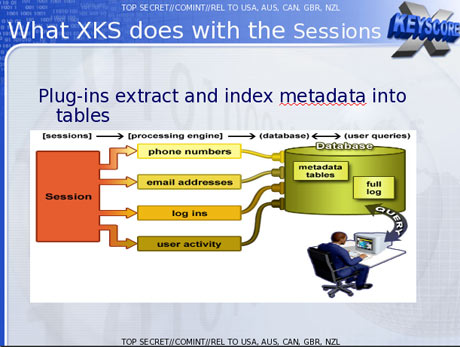
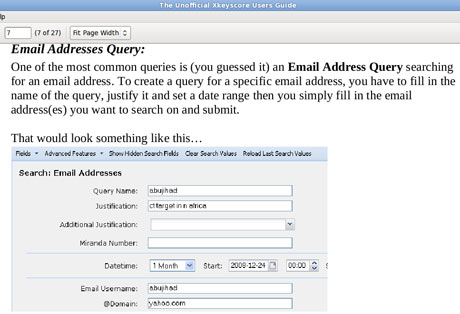
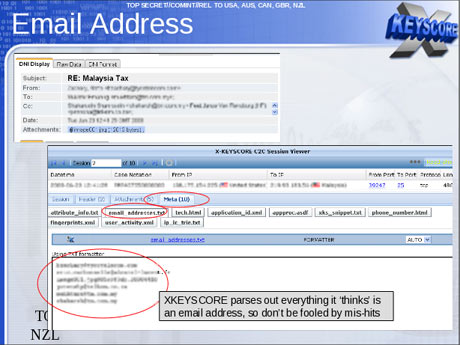
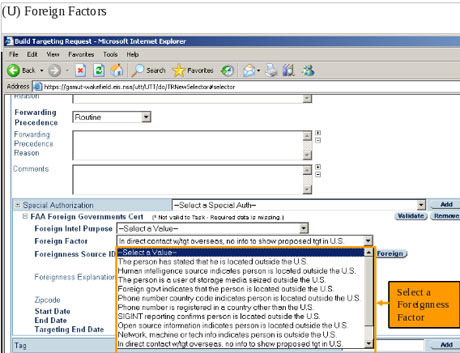
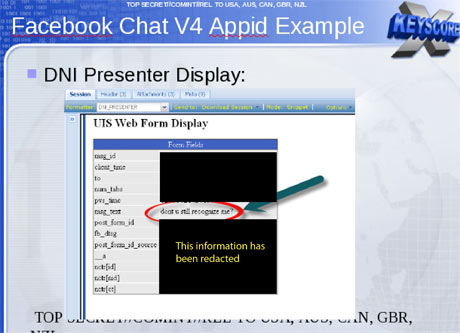
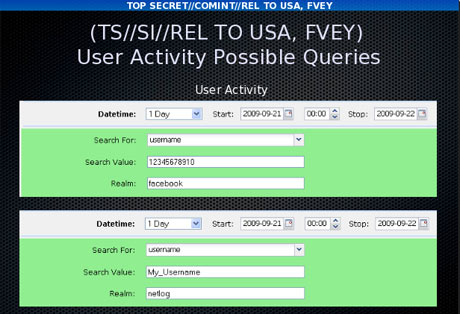
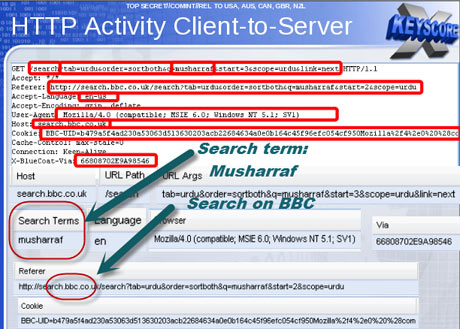

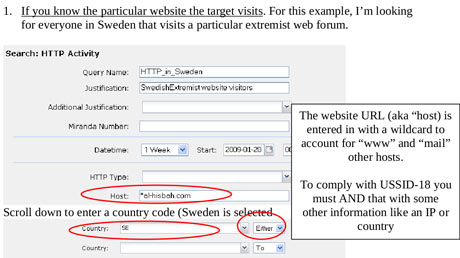
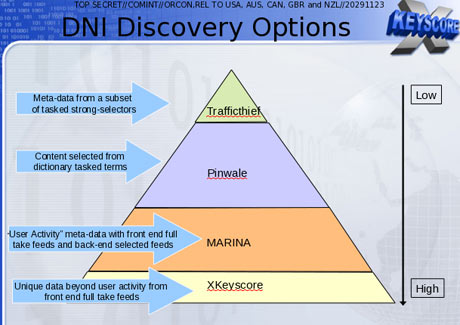
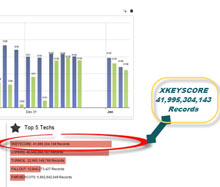
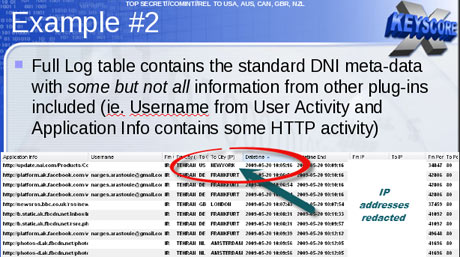



 One
day, as I surfed the web on my laptop and lamented how long it takes a
YouTube video to load, I found myself wondering if employees of the US
government — DoD researchers, DoE scientists, CIA spies — are also
beholden to the same congestion and shoddy peering that affects everyone
else on the internet. Surely, as hundreds of scientists at Fermi Lab
near Chicago wait for petabytes of raw data to arrive from the
Large Hadron Collider in Europe, they don’t suffer
interminable connection drops and inexplicable lag. And, as it turns
out, they don’t: the US government and its national laboratories all
have exclusive access to ESnet — a shadow internet that can
sustain 100-gigabits-per-second transfers between any of the major
Department of Energy labs. And today, the DoE announced that the
100-gigabit ESnet will be extended across the Atlantic to our Old World
comrades, who occasionally manage to dazzle us with their scientific
endeavors.
One
day, as I surfed the web on my laptop and lamented how long it takes a
YouTube video to load, I found myself wondering if employees of the US
government — DoD researchers, DoE scientists, CIA spies — are also
beholden to the same congestion and shoddy peering that affects everyone
else on the internet. Surely, as hundreds of scientists at Fermi Lab
near Chicago wait for petabytes of raw data to arrive from the
Large Hadron Collider in Europe, they don’t suffer
interminable connection drops and inexplicable lag. And, as it turns
out, they don’t: the US government and its national laboratories all
have exclusive access to ESnet — a shadow internet that can
sustain 100-gigabits-per-second transfers between any of the major
Department of Energy labs. And today, the DoE announced that the
100-gigabit ESnet will be extended across the Atlantic to our Old World
comrades, who occasionally manage to dazzle us with their scientific
endeavors.











