The Matrix Is Real & Here – US Ignite Is The Biggest Threat To Human Freedom & Will Burn Down America
by Pete Santilli, Investigative Journalist & Host of The Pete Santilli Show For
almost 2 years, my co-host Susannah Cole has been patiently insistent
on getting my attention about U.S. Ignite. Almost every issue we cover
on The Pete Santilli Show is impacted and/or influenced by U.S. Ignite,
but when I began looking into the program, I couldn’t wrap my mind
around the enormity of the initiative.
For
almost 2 years, my co-host Susannah Cole has been patiently insistent
on getting my attention about U.S. Ignite. Almost every issue we cover
on The Pete Santilli Show is impacted and/or influenced by U.S. Ignite,
but when I began looking into the program, I couldn’t wrap my mind
around the enormity of the initiative.At a first glance, I understood how U.S. Ignite was tied directly and indirectly to Obamacare in many different respects. Early in my findings, I focused my energy on the detrimental elements of ObamaCare, and quite frankly I considered ObamaCare the top-level parent of the potential hazards of U.S. Ignite.
As I now understand it, Obamacare is merely a “tentacle of the U.S. Ignite octopus”.
When I received news recently regarding the merger between Comcast and Time-Warner, my hackles of curiosity were raised once again, and U.S. Ignite immediately came to mind. From my perspective, I saw U.S.Ignite as the central hub connected to ObamaCare, Verizon/AT&T telecommunications industry, as well as the media industrial complex especially when I realized there is no possible way to stop the monopolistic merger of Comcast and Time Warner. Needless to say, the Comcast Time-Warner merger stopped me in my tracks when I discovered that Barack Obama is golfing buddies with Comcast’s CEO. The deal is done, and it immediately became obvious to me that it is one of the final steps to implementing U.S. Ignite.
On February 14, 2014, I started digging into my stored library of U.S. Ignite resources I hadn’t looked at over the past several months. That isn’t to say that Susannah Cole hadn’t mentioned U.S. Ignite on many occassions when the topics warranted. In almost every instance, we were referencing U.S. Ignite when discussing Obamacare, frequently linking the “cradle-to-grave” monitoring aspects of Obamacare. To us, we naively thought the fearful death panel was U.S. Ignite’s telecomm-tether system which transmits vital statistics to the ObamaCare database, and when a senior citizen reaches obsolescence, Obamacare would — in essence — pull the plug on an unproductive 65 year old “useless feeder”.
Finally, after almost 2 years of Susannah Cole’s insistence that I fully understand the full implications of U.S. Ignite, the light came on. I asked myself, “who the heck started this ‘U.S. Ignite” thing?” and I began digging. I quickly began peeling back layer after layer, and I will state this for the record. As of this writing, what I discovered is so shocking; so startling; and so awakening, that I realized almost everything I have done up to this moment of discovery has prepared me to understand the full implications of U.S. Ignite. Since a young age, I have acquired extensive experience in computer technology, manufacturing and engineering, telecommunications, military/weaponry, surveillance, media/marketing, and within the past several years as an investigative journalist, environmental issues, mind control technology, neuro-linguistic programming, Obamacare, education and energy. My life experiences have helped me understand what I discovered when I stumbled into the “Genesis”, or origination of the U.S. Ignite initiative.
What I discovered will shock the world, but it’s not just the controlling elements of the U.S. Ignite initiative which are startling. The program is here, in full motion, in it’s final stages of implementation, irreversible, and has been developed since 1987. It’s ‘The Matrix’ of the future we’ve all been fearing and waiting for, but that’s not the most shocking revelation. Since 1987/1990, the U.S. Government has been advancing the initiative unopposed and without any consideration whatsoever for it’s unconstitutionality.
Please allow me to be as succinct as I possibly can in describing U.S. Ignite: It’s a new, secondary high-speed internet designed to replace the original internet we know today. The present day internet is the old; obsolete, slow system we inherited from the military industrial complex in the late 80′s. The U.S. Government knew it was a beast, but in order to accomplish their goal of implementing an all-encompassing technological system of enslavement, they had to come up with a way to pay for the research and development. The costs back then were considered enormous for what they intended to do, and their intentions are now very transparent as they reach the final stages.
Look at the Central Intelligence Agency and their methods of mind control developed over the past 50+ years. Take a look at the NSA, their computing power of surveillance, and their total disregard for human rights. The military industrial complex has now fully metastasized into a stage-4-cancer equivalent of a tumor attached to the entire world, and the prognosis for survival is terminal. The new techno-tronic system of enslavement we live in can be described as the military-media-medical-industrial-complex; better known as The Matrix. Look into the history of U.S. Ignite and you will quickly discover that the U.S. government — which built and will govern The Matrix —- gave the initiative a fascist marketing buzzword, but the best way to accurately describe it is to call it every hyphenated industrial complex in existence.
The Genesis of U.S. Ignite
Our GMN investigative journalists and researchers have assembled a very valuable resource for following the timeline or chronology of events which led up to the present day U.S. Ignite initiative. We call it the U.S. Ignite Link Library, and we will continue to provide links and data on this page as we continue our research. The information is overwhelming, but we believe it’s important to at least have a centralized resource that every individual can reference. The bottom line of our discovery is that there is no central source of material or critical opposition to U.S. Ignite. It’s stunning to discover that The Matrix has been funded, designed and implemented unchecked, unopposed, unconstitutionally, and until now, undetected.
When you dig; dig; dig into the history of the initiative, you ultimately end up in one place in time and space. Around 1987, the military and the government had already decided to introduce the “internet” to the public for educational and commercial applications. They knew it would spark an information technology revolution, but at the same time, they knew that their top secret work in areas of mind control, human enslavement, and global military/political dominance would require a much fast system than the old, obsolete hunk-of-junk they were releasing to the public domain.
Please read CNRI & GigaBit Testbed Initiative which is excerpted below. (Even if it’s “boring” reading, we suggest you visit and at least know where to reference back to when you discover less boring information down the path of your learning). This report is at the top of the U.S. Ignite Link Library, and I consider it to be ground zero, or the Genesis of our path towards destruction.Let me translate the information you just read in what I always refer to as “meat-and-potatoes” language that everyone can understand. The military built the internet in the 60′s, while at the same time they developed some high-tech stuff in the laboratory to lock down the entire planet of useless eaters. The system became old and obsolete, but to build a faster system (gigabit speed), it would be too expensive. There aren’t enough slave workers in the USA, nor was there enough cocaine or heroin users to generate tax or C.I.A. drug dollars to support the system they needed. So, they pawned off the old system to the public in the 1990′s. The dot-com boom was born, we were told it was invented by Al Gore, and everyone said WOW.
This report summarizes the results of the Gigabit Testbed Initiative, a project involving several dozen participants that ran from 1990 to 1995. The report attempts to put these results into perspective by providing the background, motivation, and current trends impacting the overall work. Detailed descriptions of context and results can be found in the final reports from each of the five testbeds involved in the Initiative [2-6] .
The Initiative had two main goals, both of which were premised on the use of network testbeds: (1) to explore technologies and architectures for gigabit networking, and (2) to explore the utility of gigabit networks to the end user. In both cases the focus was on providing a data rate on the order of 1 Gbps to the end-points of a network, i.e., the points of user equipment attachment, and on maximizing the fraction of this rate available to a user application.
A key objective of the Initiative was to carry out this research in a wide-area real-world context. While the technology for user-level high-speed networking capability could be directly achieved by researchers in a laboratory setting circa 1990, extending this context to metropolitan or wide-area network distances at gigabit per second rates was virtually impossible, due both to the absence of wide-area transmission and switching equipment for end-user gigabit rates and to the lack of market motivation to procure and install such equipment by local and long-distance carriers.
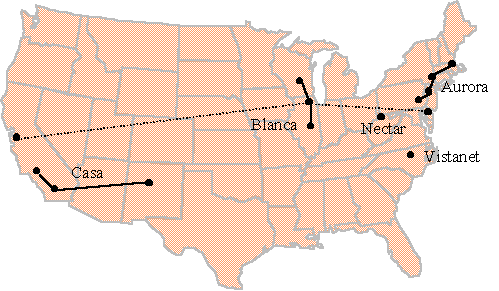
To solve this “chicken-and-egg” problem, a collaborative effort involving both industry and the research communities was established by CNRI with funding from government and industry. NSF and DARPA jointly provided research funding for the participating universities and national laboratories, while carriers and commercial research laboratories provided transmission and switching facilities and results from their internally-funded research. Five distinct testbed collaborations were created. These were called Aurora, Blanca, Casa, Nectar, and Vistanet. (A sixth gigabit testbed called MAGIC [7] was funded by DARPA about 18 months later, but was managed as a separate project and is not further described in this report.)
Computer networking dates from the late 1960s, when affordable minicomputer technology enabled the implementation of wide-area packet switching networks. The Arpanet, begun in 1969 as a research project by DARPA, provided a focal point within the U.S. for packet network technology development. In the 1970s, parallel development by DARPA of radio and satellite-based packet networks and TCP/IP internetworking technology resulted in the establishment of the Internet. The subsequent introduction and widespread use of ethernet, token ring and other LAN technologies in the 1980s, coupled with the expansion of the Internet by NSF to a broader user base, led to increasing growth and a transition of the Internet to a self-supporting operational status in the 1990s.
The Gigabit Testbed Initiative was a major effort by approximately forty organizations representing universities, telecommunication carriers, industry and national laboratories, and computer companies to create a set of very high-speed network testbeds and to explore their application to scientific research. This effort, funded by the National Science Foundation (NSF) and the Defense Advanced Research Projects Agency (DARPA), was coordinated and led by the Corporation for National Research Initiatives (CNRI) working closely with each of the many participating organizations and with the U.S. Government. The U.S. Government was also a participating organization insofar as testbeds were established within several Government laboratories to explore the concepts and technologies emerging from the Initiative.
Little did the entire population know that we’d all become farm animals on the old internet providing energy and innovation to produce the new internet which DARPA and the “NSF” (DARPA’s sister or spouse; or both if you believe it originated in Kentucky) set out to build since the late 80′s.
The U.S. government essentially decided to use $20 million dollars to spark “innovation” among corporations who were clamoring over market share and wealth in the dot com boom. The government needed to build out The Matrix which would totally enslave the entire human race by controlling energy/environment, education, communication, surveillance, the human mind, healthcare, manufacturing, media, and homeland security. What they had to do was compartmentalize each element within the various industries of each of the elements of their desired total control, and initiate the process of innovation and voluntarily acceptance by the public. The US Government set out to create entire economies of scale that would innovate, engineer, market and profit and ultimately become a vital contributor to The Matrix…without the government spending a dime. The CNRI Corporation for National Research Initiatives (CNRI) “worked closely with each of the many participating organizations and with the U.S. Government.”.
Simply translated: THE MATRIX WAS BUILT BY FASCISM WITH COVERT INTENTIONS. We farm animals have been clicking away, carrying phones, inputing every thought, and designing new efficient means of eliminating the jobs of everyone around us. Better, bigger, faster, smarter…like a bunch of little energetic mice on a conveyor belt.
Who Started This “Initiative”?
Who started this whole thing? Of the many culprits, the most blame can be directed at the NSF (National Science Foundation). The NSF is to The Matrix as DARPA is to robots. Consider the NSF the computer specialists and DARPA mechanical engineers. In my mind, the NSF is even more dangerous than DARPA, and the while “the-powers-that-be” have had us focused and fearful of dark DARPA projects, the NSF has been coordinating the buildout of The Matrix.
The National Science Foundation (NSF) is an independent federal agency created by Congress in 1950 “to promote the progress of science; to advance the national health, prosperity, and welfare; to secure the national defense…” With an annual budget of $7.2 billion (FY 2014), we are the funding source for approximately 21 percent of all federally supported basic research conducted by America’s colleges and universities. In many fields such as mathematics, computer science and the social sciences, NSF is the major source of federal backing.How Did The Old Internet Fuel The Build-Out of The Matrix?
In their 2011-2016 Strategic Plan, the NSF Act set forth a mission: “to promote the progress of science; to advance the national health, prosperity, and welfare; to secure the national defense; and for other purposes.“
Obviously, the entire world has benefitted from almost every aspect of the internet revolution. There’s no disputing the fact that our lives have improved in many respects. None of us can really complain about it’s revolutionary benefits and production.
What none of us have realized is (a) how intrusive it would become (b) that our privacy would be obliterated and (c) that we as humans would become the “product” that corporations profit from
The innovation and engineering in telecommunications, media, healthcare, etc. has been explosive, and entire economies have been built on improvements and advances in each industry.
Here’s the hidden secret: None of us knew what the government’s ultimate goal was. The government knew from the start that the old system was obsolete; especially for what they wanted to use it for. None of us knew that their idea was to energize corporations to start, build and grow, “create jobs” that would ultimately eliminate jobs, use the profits for research & development at the speed of the internet, and do all of this on the back of the human population. The advancement in technology and understanding of the human mind would be poured into a centralized system that creeped forward with the help of the partnership between government and business.
The parallel “INTERNET 2″, a high speed; gigabit infrastructure would be built as the old internet evolved with the energy of human input. We “farm animals” have been clicking away, telling the world our thoughts, frappa Latte’s and meals, and ultimately making the INTERNET 2 much smarter than it ever could have been without our free slave labor. Heck, Google, Facebook and Twitter even figured out how to read our minds an put advertisements in our face as we worked for them for free. We click on the ad, and the advertiser pays them. The old, obsolete, slow internet has been making them money hand over fist. All they need now is to do it faster, and to force all of us to make them smarter.
If a human knew he was being used as a mouse on a conveyor belt, providing energy and profit to an evil entity, do you think he would have worked so hard?
If a corporation knew it was being used as a cog in the wheel; turning faster and faster towards enslavement of the human population, do you think they would have been so willing to become “partners” in any government venture or initiative?
Well, the NSF and the CIA knew the answers to those questions, so they had to maintain the world’s best kept secret since the late 80′s. All of us have been ‘virtually’ volunteering to build our own concentration camp of the internet, and we never really have to leave the comforts of our own homes or businesses.
Let’s Fast Forward to June 2012
Barack “Barry Soetoro” Obama (depending on which part of the internet you’ve been corralled to and brainwashed) releases an Executive Order, and the press release was titled:
We Can’t Wait: President Obama Signs Executive Order to Make Broadband Construction Faster and Cheaper
The first paragraph reads as follows:Tomorrow, the President will sign an Executive Order to make broadband construction along Federal roadways and properties up to 90 percent cheaper and more efficient. Currently, the procedures for approving broadband infrastructure projects on properties controlled or managed by the Federal Government—including large tracts of land, roadways, and more than 10,000 buildings across the Nation—vary depending on which agency manages the property. The new Executive Order will ensure that agencies charged with managing Federal properties and roads take specific steps to adopt a uniform approach for allowing broadband carriers to build networks on and through those assets and speed the delivery of connectivity to communities, businesses, and schools.Now, if you hadn’t researched or read any of the above history, you would assume by reading the title and the first paragraph that Obama’s neat idea was fresh, hip, new and absolutely so critical that it couldn’t wait for the Congress, Supreme Court, or the public, and he HAD to sign an Executive Order.
Obama was so hurried and excited, that he HAD to convene a meeting at the White House. The very next day, the US Ignite Initiative launch took place at the White House (see the video of the entire launch), and Obama released a “Broadband Fact Sheet 06-13-2012” which made it sound like the NSF was jumping on board —as if they received an email the day before:
National Science Foundation (NSF) Leverages Investments in Virtual Laboratory to support US Ignite
As the lead Federal agency for US Ignite, NSF will expand its initial 4-year, ~$40 million investment in the Global Environment for Networking Innovations (GENI) project
Since we HAVE read this article and the links attached, we now know
that there is evidence that the NSF has been working on this launch
since 1987. The so-called “President” not only could have waited to let
everyone know what he was up to, his White House has known since way
before the 1960′s what this “exciting new project” was all about.
It was the perfect scenario, and since the Patriot Act/ 9-11 / DHS
method of taking over every little town in the USA, we now see how the
government operates to get the job done: They get secrecy and
compliance with big bags of cash. The NSF has spent countless sums of
money with Corporations who take it willingly. No hesitation from the
public as well — heck, everyone has a new iPhone or ObamaPhone
(depending on which side of town you live, and which color you support
in the White House).
Unopposed, Unchecked, Unconstitutional
One of the biggest parts of this story is how this was done with
trillions of dollars, billions of mice, over several decades….under the
radar. Every branch of government, corporation and citizen allowing a
select few lunatics in the CIA and NSF to build a multi trillion dollar
system of bondage & enslavement. Volunteering to surrender
everything – life, liberty, and pursuit of happiness — all under the
guise of “creating jobs” and “being #1″ in the United States of America,
home of the brave, land of the free.
Not one politician has come forth to disclose what this system is,
and they know better. Even Ron Paul understands the power of the
internet. Not a peep from him, and he’s been around since this thing
was started.
Not one member of the main stream media (of course not, you might
as well have a perpetual price tag and receipt on them — they have
always been bought & paid for)
Not one member of the so called “Alternative Media” has called this
out, and as a member of the Independent Media, I feel I have an
obligation to let my fellow man & woman know about it.
Why Worry About US Ignite & GigaBit Fast Internet 2?
These are facts: Google monitors and stores every single search and
website you have visited. Google, Twitter and Facebook all provide
their data to a company called Palantier (means ‘seeing stone’) and
Palantier’s function is to do predictive analysis based on our human
input and interaction with computers. Based on what we are typing,
saying and searching, not only do marketers/companies know what to sell
us, the government knows how to manipulate our opinions and thoughts.
At the speed of fiber optic light, every single spoken word in your
home, place of business, car, on the phone, in private, etc. is sent
into The Matrix. If you haven’t seen the movie The Matrix, go watch it
and remember how the Agents always know where to find Neo.Almost every high speed gadget and application which has been developed by companies are AWESOME! and in high demand. The innovators are geniuses. They all have great intentions, and are very successfully contributing to making our lives “better”. Little do they know, their advancements are being used for the common evil purposes of what US Ignite was initiated for.
How do we know? Because they wouldn’t have kept everything I am describing in this article a secret for so many years. If the NSF’s, DARPA’s and the CIA’s intentions were good, then why would we keep all of this information from the public for decades?
Please allow me to answer: Because once they’ve turned the switch on and finally tell the public, each of us will be under their absolute control forever. No freedom of speech. No freedom of movement. No freedom of thought. No freedom of religion. No right to defend ourselves. Nothing God ever gave us will be allowed. We will worship our new God…The Matrix….just ask the Matrix if what I am saying is true and you will see that I am 100% right. Do you have any Energy, Education, Telecomm, Surveillance, Mind Control, Obamacare, Manufacturing, Media, DHS, Environmental concerns? No need to call upon your God, US Ignite has everything under control (pun intended).
Conclusion
This concludes what is undoubtedly the very first opposing article written against US Ignite, but certainly not my last. This is the beginning of a journey, and I ask you to join me. We need every single member of the main stream media, alternative media, independent media, new media, and citizen media to learn as much as they can, and share their findings.
Can any of this be stopped? Absolutely not. The only thing we can do is remember how they defended themselves in the movie The Matrix. Only an EMP will save us. The “squiddies” are coming, and there is absolutely no way to stop them other than to temporarily render them electronically inoperable. Even an EMP over the USA won’t stop them. Although we’d be sent back to the 1800′s, they likely have a way to get us back up and running in a few weeks.
Should our goal be to stop them? I don’t believe so. As I said earlier : If a human knew he was being used as a mouse on a conveyor belt, providing energy and profit to an evil entity, do you think they would have worked so hard to get us here? If a corporation knew it was being used as a cog in the wheel; turning faster and faster towards enslavement of the human population, do you think they would have been so willing to become “partners” in any government venture or initiative?
My goal is to at least treat humans as they deserve to be treated, and to do everything we can to preserve our inalienable rights — and we obviously don’t need a piece of paper to back it up, especially since the one we have is virtually useless.
Let’s just tell everyone what they’re up to and piss them all off. It seems that the only power they have is secrecy, so let’s expose them & watch them die from the agony of being found out. For me, my dream is to die a free man, and be known for pissing them all off.