The US National Security Agency (NSA) is building the foundation for a global police state. This is not an exaggeration.
The lynch pin of the NSA system is the continuous gathering of
all types of digital data on political leaders, economic institutions,
and hundreds of millions of people around the world. Despite the recent
revelations, the political leaders of the US government have never
stated that such activities will stop.
However, the current massive cyber surveillance of the worlds’
people and institutions is only the beginning of the threat from the NSA
and its allied US government agencies. Unrestricted information
technology (IT) power in the hands of the US government is a future
threat which dwarfs anything the NSA has done to date.

AFP Photo / Paul J. Richards
Moore’s law, a prediction originally formulated by Intel co-founder
Gordon Moore, states that microchips double in power and halve in price
per unit power every two years. In the 47 years since this prediction
appeared, it has always been validated, and experts expect this
trajectory to continue for the foreseeable future.
By simple arithmetic of the 2x2x2x2x2 variety, we can see that ten
years from now, chip power will be 32 times greater than today. The
capabilities of a wide range of digital devices will also improve
exponentially, as processing speed, memory capacity, sensors, and
miniaturization are all linked to Moore’s law.
This upward leap will have massive negative consequences if the US
government is permitted to retain its current ‘blank check’ on the use –
and manipulation – of IT.
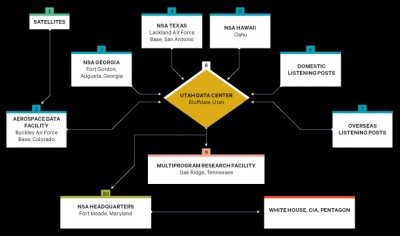
To begin with, the power to gather – and to automate – the scanning
and manipulation of…the worlds data will grow exponentially. The NSA has
already anticipated this development by constructing a gigantic new
center in the US state of Utah. Finished at the end of 2013, it will
house unimaginable amounts of data – amounts far greater than any it has
so far gathered, at an estimated cost for construction plus hardware
and software of 3.5 to 4 billion US dollars.
Second, the power of the NSA – and of other US government entities –
to instantlycontrol or kill anyone or any institution anywhere in the
world will also grow exponentially. IT-controlled pilot-less drone
airplanes, currently used by the US government to murder people
thousands of miles away in a number of countries, are but a small
harbinger of what will be possible.

AFP Photo / Mario Tama
One important development is what IT people call
‘the internet of things,’
something which is already under construction. The idea is to
incorporate into the world network a large proportion of the inanimate
objects which surround us. Grocery store products, appliances, vehicles,
buildings, highways, factory systems, and machines, and more are all
being added – or will be added – in various ways to the network. Many of
these things, of course, already contain computer chips, and some are
already networked.
Building backdoors and hacking – methods beloved by the NSA – into the chips, software, and network connections of this
‘world of things’ would turn everyday objects into potential drones.
Imagine, for example, a foreign government official is disliked by
the US government – or just by the NSA. Or perhaps someone in the US
posts something on the internet that the government really dislikes.
Suddenly, that person is attacked by their toaster. Or they mysteriously
lose control of their car. Or the airplane they’re flying in crashes.
Or the friendly house-cleaning robot they recently bought suddenly turns
mean.
On a larger scale, the same kinds of methods can be used to disrupt
or put out of action a foreign country’s military systems, government
systems, or economic enterprises.
What’s more, there is every possibility that the NSA or similar
agencies will attempt to infiltrate their spying, and potential for
disruption, into the emerging realm of augmented reality technologies.
Augmented reality involves looking at a real-world environment through
an IT-enhanced pair of glasses – glasses which simultaneously display
the real world and some digital content such as images, pictures, text,
video, or whatever. Moreover, these glasses are connected wirelessly to
the internet, so the augmented realities can be shared.
To cite a very simple example, you might be looking at a real world
table, but seeing flowers on the table that aren’t there. And you might
be seeing and talking to people at the table who are actually in another
place.
This isn’t science fiction; it’s on the way in various forms to
widespread commercial availability in the next year or so from multiple
IT companies – including Google, and several dozens more. Some experts
believe that functions now done on computers, mobile phones, and other
IT systems currently in use will ultimately ‘collapse’ into, or be
absorbed into, this new technology.

AFP Photo / Hoang Dinh Nam
As wonderful as it may prove to be, augmented reality technology is
also not without dangers. Bear in mind the recent revelation that the
NSA has already infiltrated false
‘avatars’ and engaged in
other covert activity in World of Warcraft and Second Life, two of the
most popular multi-player computer game systems, in which users immerse
into a ‘virtual world.’ Such games are are used by millions of people
around the world.
Information technology – powered by Moore’s law – is, in fact, moving
progressively closer to the human brain. From the post-WWII mainframe
computers, to desktop computers, to notebooks and tablets, to
smartphones, to augmented reality glasses.
What’s next? The logical step beyond the glasses is apt to be
something like augmented reality operating through contact lenses,
followed after that by augmented reality operating through actual visual
and auditory implants behind the eyes and ears, thereby creating real
world
‘augmented humans.’ Such technology might greatly
increase the capabilities and even intelligence of users. But it also
has a dystopian potential for unprecedented state spying and
interference.
Under ever-worsening life conditions for the American people, there is a real danger that IT-enabled
‘security’ – whether called the
‘NSA’
or something else – will increasingly be used for more illegal and
unconstitutional surveillance and control of the population. Only a
determined effort now to rein in the NSA – and the massive use of IT for
so-called
‘security’ purposes – can help prevent this potential tragedy.







 Pat Dollard
Pat Dollard