Evil genius behind the Flashback OS X trojan may have been uncovered
Leaked messages show man taking credit for malware that infected 650,000 Macs.
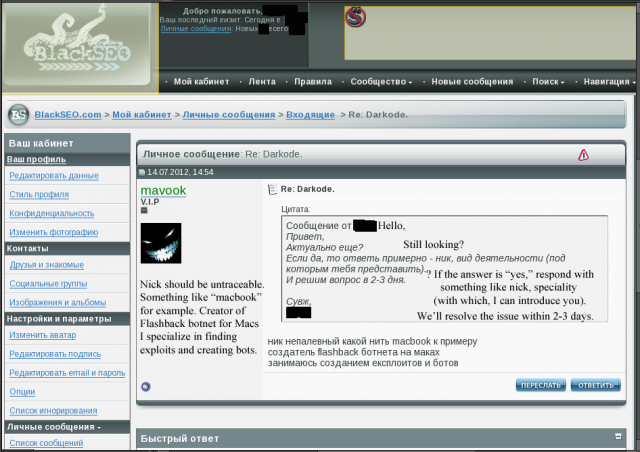
A private message taken from BlackSEO.com
in which a user named "Mavook" takes credit for the Flashback trojan
that infected 650,000 Macs.
Flashback.K, as that version was known, was a breakthrough because it was among the first pieces of mainstream malware to hijack Macs even when users didn't enter an administrative password. Rather than trick users into installing what appeared to be an update to the Adobe Flash program—as previous Flashback versions did—this new release exploited a security bug in Apple's version of the Java software framework. Users who had it installed and visited booby-trapped websites were infected with no warning. Even after Apple released software to remove Flashback, the malware was still able to thrive in the following weeks, expanding its infection base to 650,000 machines.
Until now, there have been no public clues about the identity of the evil genius who was responsible for Flashback. Researchers knew the malware was able to earn as much as $10,000 per day by redirecting Google search results to third-party advertisers. Acting on this knowledge, Krebs began scouring the underground forums on BlackSEO.com, a site frequented by blackhat experts in search engine optimization.
The first clue came in a private message on July 14 between a VIP BlackSEO.com user named "Mavook" and a top forum member of the site. In it, Mavook asked for help in becoming a member at Darkode.com, another underground forum frequented by online miscreants. To demonstrate the criminal bona fides needed to gain entry into the elite forum, Mavook volunteered that he was the "creator of the Flashback botnet for Macs" and added: "I specialize in finding exploits and creating bots."
Krebs unearthed another private message, in which the same senior member vouches for Mavook to another BlackSEO.com user, who had been looking for an experienced software exploiter. The senior member, who had already become well-acquainted with Mavook's work, eventually responded: "If Mavook won't budge, saying that he is no longer doing this stuff, write to me again."
Krebs then followed a series of digital breadcrumbs left on Mavook's profile page and elsewhere. It turns out that his personal home page was once at mavook.com, a site that was originally registered in 2005 by one Maxim Selikhanovich in the Russian city of Saransk. The registrant of the site used the e-mail address h0mini@mail.ru. A search of Skype users showed that address brought up someone with the screen name of Maximsd. Krebs also uncovered the address mavook@gmail.com, which is also tied to someone named Maxim Selikhanovich, according to registration records for a now-defunct website, saransk-offline.com.
The Hotmail address was also a contact point for mak-rm.com, which belonged to a Saransk-based IT-outsourcing and Web design firm called Mordovia Outsourcing Company. The domain is registered to one "Max D. Sell" in Saransk. Krebs cited a trusted source with the ability to look up tax information on Russian citizens and corporations as saying Mordovia Outsourcing Company was registered and founded by a "Maxim Dmitrievich Selihanovich, a 30-year-old from Saransk.
To be fair, the case Krebs builds is largely based on private messages that presumably were leaked by insiders or people who hacked the forums. The information is only reliable if the original material is authentic and if the user Mavook was being truthful when taking credit for Flashback. The leaks come one day after Krebs exposed behind-the-scenes communications taking place on Darkode, suggesting a much larger leak or compromise by insiders.



No comments:
Post a Comment