Kingpin behind large chunk of world’s malware exploits led lavish life
Russian prosecutors confirm arrests connected to BlackHole Exploit kit.
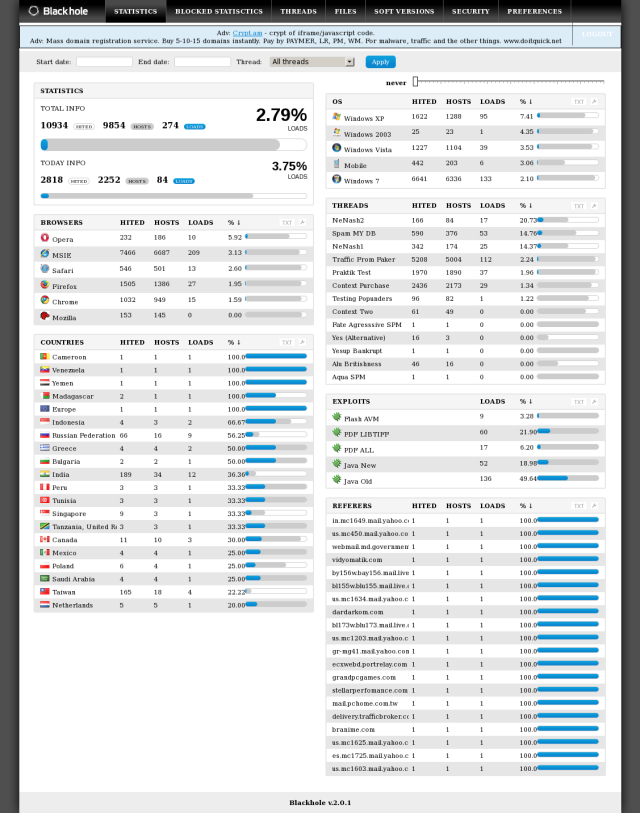
Enlarge / A screenshot showing BlackHole statistics.
The 27-year-old Russian, identified only as Paunch, allegedly earned about $50,000 per month selling BlackHole subscriptions for as much as $500 per month, according to a report published Friday by security firm Group-IB. He is also alleged to be behind the much more expensive Cool Exploit Kit and a "Crypt" service used to obfuscate malware to go undetected by antivirus programs. With more than 1,000 customers, he was able to lead a lavish lifestyle that included driving a white Porsche Cayenne, Group-IB said.
Enlarge / A man Group-IB identifies as "Paunch" standing in front of a Porsche Cayenne.
The Group-IB report came the same day the Russian Interior Ministry confirmed the arrests in October of 13 individuals that it said took part in the "dissemination of malicious software ('banking Trojans'), followed by unauthorized access to legally protected computer information (logins, passwords, electronic keys, certificates)." The statement didn't name Paunch or anyone else by name or handle, but it did say the group was connected to BlackHole. The statement came two months after a former police detective in Russia told Reuters that Paunch had been arrested. It's unknown if Paunch has made a court appearance or issued a plea of guilty or not guilty.
According to Group-IB, Paunch worked with others to stockpile exploits, which typically target programming bugs in Internet Explorer, Oracle's Java software framework, Adobe's Reader and Flash applications, and other widely used programs. Group-IB said one alleged colleague, a third-party exploit broker who went by the handle J.P. Morgan, sent out a series of posts in underground crime forums announcing a budget of $100,000 to purchase exploits targeting unpatched and undocumented "zero-day" vulnerabilities. He later increased his war chest to $200,000. KrebsonSecurity's Brian Krebs said the budget eventually reached $450,000.
Russian officials estimated that the BlackHole defendants inflicted damage of about 70 million rubles, equivalent to about $2.13 million based on current exchange rates. Krebs makes a convincing argument about why the real sum is likely much higher, since BlackHole was the driving force behind an entire ecosystem of other crimeware titles including ZeuS and Citadel.




No comments:
Post a Comment