Your USB cable, the spy: Inside the NSA’s catalog of surveillance magic
Latest batch of documents from Snowden shows NSA's power to pwn.
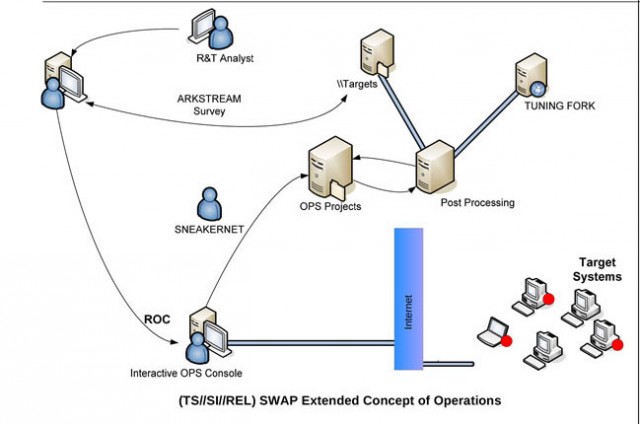
A diagram of an NSA BIOS-based attack, brought to you by sneakernet.
In some cases, the NSA has modified the firmware of computers and network hardware—including systems shipped by Cisco, Dell, Hewlett-Packard, Huawei, and Juniper Networks—to give its operators both eyes and ears inside the offices the agency has targeted. In others, the NSA has crafted custom BIOS exploits that can survive even the reinstallation of operating systems. And in still others, the NSA has built and deployed its own USB cables at target locations—complete with spy hardware and radio transceiver packed inside.
Documents obtained by Der Spiegel reveal a fantastical collection of surveillance tools dating back to 2007 and 2008 that gave the NSA the power to collect all sorts of data over long periods of time without detection. The tools, ranging from back doors installed in computer network firmware and software to passively powered bugs installed within equipment, give the NSA a persistent ability to monitor some targets with little risk of detection. While the systems targeted by some of the “products” listed in the documents are over five years old and are likely to have been replaced in some cases, the methods and technologies used by all the exploit products could easily still be in use in some form in ongoing NSA surveillance operations.
Special delivery
There’s no indication from the documents that the manufacturers played any role in the development or delivery of the backdoors (something that manufacturers are now loudly telling their customers, too). The documents, which appear to be pages from a catalog of capabilities provided by the NSA's ANT division for the NSA’s Tailored Access Operations (TAO) division, show that many of the tools on offer are ordinary Windows exploits designed to use parts of the operating system to “phone home” to the NSA with data; like most malware, these packages can be dropped in place remotely and are probably the least interesting of the new revelations.Hardware- and firmware-based backdoors, by contrast, require laying hands on the actual target systems. In some cases, the NSA’s operators install backdoor hardware and firmware directly onto the systems by “interdiction”—the systems are diverted during shipping to “load stations” where the surveillance components are installed. (This interception may have been accomplished with the cooperation of shipping companies or other government agencies; details of the process remain murky.) In other cases, the NSA uses an insider with a USB device or remote access tools deployed by other means to gain access to computer systems, allowing the NSA to “reflash” their low-level BIOS firmware.
Either way, the altering of systems’ firmware or hardware gives the NSA the ability to install backdoors that can survive a total operating system wipe and re-installation. One BIOS attack, called SWAP, was developed by the NSA to attack a number of types of computers and operating systems by loading surveillance and control software at boot-up. SWAP uses the Host Protected Area on a computer’s hard drive to store the payload and installs it before the operating system boots.
More specialized BIOS attacks were developed to take advantage of motherboard-based System Management Mode (SMM) capabilities on Dell and Hewlett-Packard servers. Dell PowerEdge servers were targeted with an implant called DEITYBOUNCE, while HP Proliant 360DL G5 servers were targeted with one called IRONCHEF. Both allowed NSA operators to gain remote control of systems in SMM mode—giving the agency firmware-level control over infected servers and the ability to do things like run “rootkits” on the server operating system.

The
ANT "product" listing for IRONCHEF, the BIOS attack on HP servers,
showing an example attack scenario where remote operators use a covert
wireless network to take control of servers.
Juniper routers weren’t the only targets of these sorts of BIOS “implants,” either—firewalls and routers from Cisco and Huawei were also on the 2007 menu for firmware and software exploits. Such router exploits didn’t even require interception of the hardware but could in many cases be remotely installed by way of another hack.
For systems where a BIOS hack is impractical, the NSA has other tools to install a persistent backdoor. One, called GINSU, uses a PCI bus device installed on the computer. An implant called BULLDOZER creates a stealth wireless bridge, providing radio-based remote control of the backdoor to TAO operators. If the rootkit on the system (called KONGUR) is removed by a system re-installation, the GINSU backdoor can re-install the software on the next boot-up.

Enlarge / GINSU allows the NSA to slice and dice computers' hard drives and control them remotely over a covert radio connection.
Reach out and touch someone
An implanted wireless device is the NSA’s go-to approach for dealing with “air-gapped” networks—networks that don’t have an Internet connection for security reasons. There are a number of other implanted devices that the NSA has in its TAO arsenal, including USB and Ethernet implants that can transmit short-range radio signals and more robust implanted hardware for longer-range transmissions. These radio links create a shadow Internet that allows the NSA to move data out of an adversary’s network and into its TURMOIL and X-KEYSCORE collection system.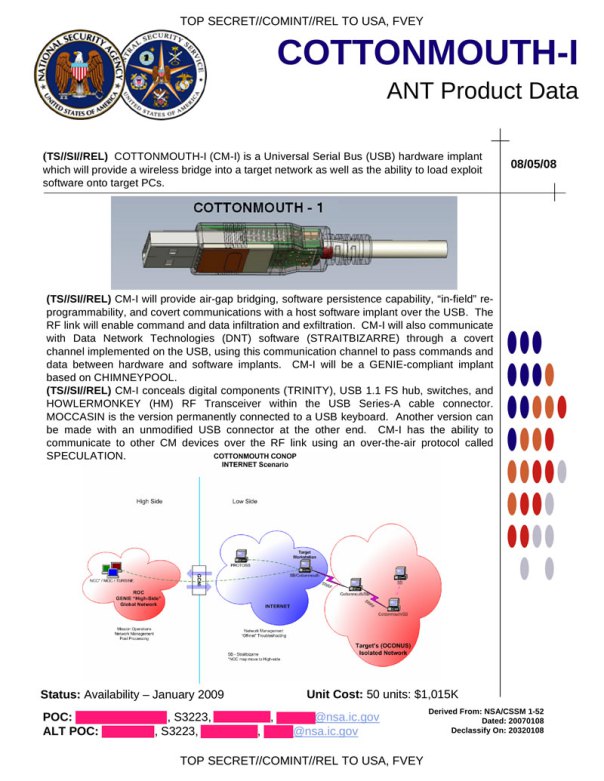
The
COTTONMOUTH series of implants are USB devices that provide a covert
wireless bridge into a target network. They can be integrated into any
USB plug, so check your mouse.

Enlarge / According to the ANT catalog, the NIGHTSTAND Wi-FI exploit system's attack is "undetectable by the user."
Hacking smartphones
The 2007 NSA wish book for analysts also includes a number of software tools that allow data to be stolen from a variety of smartphones and dumb cell phones. One software hack, called DROPOUTJEEP, is a software implant for Apple iOS devices that allows the NSA to remotely control and monitor nearly all the features of an iPhone, including geolocation, text messages, and the microphone and camera. (Researcher and developer Jake Appelbaum, who helped write the Spiegel article revealing the documents, said separately this week that the NSA claims DROPOUTJEEP installations are always successful.) Another package, called TOTEGHOSTLY, does the same for phones based on the Windows Mobile embedded operating system.Both the DROPOUTJEEP and TOTEGHOSTLY releases mentioned in the 2007 product listing required “close access methods” for installation—in other words, a human being getting up close and personal with the phone to install it. “A remote installation capacity will be pursued for a future release,” the document states. But another tool, called MONKEYCALENDAR, allowed the NSA to remotely install location-tracking software onto any GSM phone by way of a software implant for SIM cards.
But these aren't the only way the NSA can get to cell phone data. Also in the bag of tricks are a number of wireless monitoring devices, as well as “networks in a box” and other gear that can pose as cell towers and networks—intercepting devices as they enter an area and grabbing up their voice, data, and SMS traffic. A "tripwire" program called CANDYGRAM can send out alerts whenever a cell phone hits a specified cell tower.
Old tricks, new tricks
It’s important to note that the exploits in the documents are largely over five years old, so they don’t necessarily give a complete picture of what the NSA is capable of today. That doesn’t mean that these techniques are no longer in circulation—given the stubbornness of Windows XP, many of the exploits developed for older Windows platforms may have years left in them, and some of the adversaries the NSA is trying to monitor don’t have Fortune 500 hardware refresh rates.A frequent defense of what the NSA does with its bag of tricks is that in many ways it is no different from what other countries (including China, Russia, and France) try to do to the United States and other countries via their intelligence organizations. These documents show the key way the NSA is different—its vast technical resources and ability to essentially put itself into the supply chain for technology flowing to the rest of the world. US officials have long suspected China of doing the same thing with hardware from companies such as Huawei and ZTE, but these documents essentially spell out that "interdiction" is part of the US intelligence strategy, too.
The exposure of the techniques and capabilities of the NSA creates another problem for the agency, in that it provides those hard-to-get-at organizations the TAO was created to go after with an idea of how the NSA has targeted and will target them. It also creates a problem for companies like Cisco and Juniper, who now face the same sort of scrutiny the US and others put Huawei under for its connections to the Chinese military. Even if Dell, HP, Cisco, and Juniper had no hand in creating the backdoors for their products, the documents will undoubtedly be used against them the next time they try to sell hardware to a foreign government.



No comments:
Post a Comment