How to stash secret messages in tweets using point-and-click steganography
Centuries-old sleight of hand for concealing sensitive data goes mainstream.
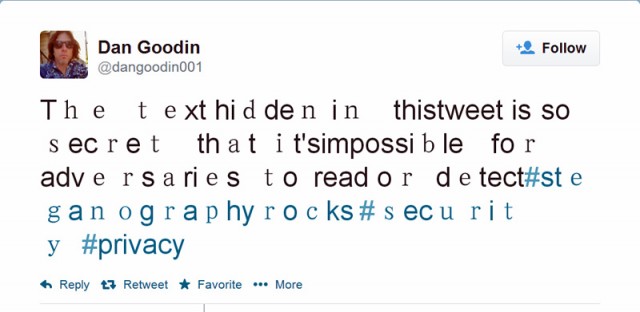
Now steganography is going mainstream with a service that embeds hidden messages inside more or less ordinary Twitter messages. Users need only type the text they want others to see in one field and the hidden message in a separate field. The service, created by New Zealand-based developer Matthew Holloway, then spits out a tweetable message that fuses the two together in a way that's not noticeable to the human eye. Take the following tweet: Dan Goodin @dangoodin001 Follow
The teⅹt hidden in thіs⁰tweet іs so seϲret that it's⁰іmpossіble for adⅴersarіes to read оr deteϲt⁰#steganographyrocks #security #privacy
Security through obscurity
Embedded in the visible message "The text hidden in this tweet is so secret that it's impossible for adversaries to read or detect #steganographyrocks #security #privacy" are the words "no, it's security through obscurity." The letters making up the secret text are expressed in unicode representations that are included in the public message. The encoding added to the messages explains the unusual spacing and fonts found in the tweet. With a little more work, or in formats not as constrained as Twitter's 140-character limit, it would almost certainly be easier to create messages that appeared less crude. The same service takes finished tweets and ferrets out their hidden cargo.While steganography has long been relied on to safeguard sensitive messages, people should realize the technique is little more than security through obscurity. That's because the embedded secret is ripe for plucking by anyone who takes the time to look for it. By contrast, ciphertext generated using strong and time-tested encryption algorithms is virtually impossible to decode without the underlying key, which can take centuries or millennia to guess using even the fastest computers. So put steganography in the same category as disappearing ink. It may even have useful applications in rare circumstances. For instance, it might be an effective technique for a prisoner of war sending a postcard to family members. If it were to include a random-appearing sequence of letters, it would be clear to captors that it included an encrypted message. If instead the POW crafted a postcard that used every fifth letter to spell a hidden message, the captors might not notice. That said, steganography is mostly fun to play with. It should never be relied on to protect digital crown jewels without a good reason and with plenty of forethought.
No comments:
Post a Comment